Microsoft has some advice on how to defend against “ice phishing” and other novel attacks that aim to empty cryptocurrency wallets, for those not already abstaining.
Ice fishing involves cutting a hole in a frozen body of water in order to catch fish. Ice phishing, as Microsoft describes it, is a clickjacking, or a user interface redress attack, that “[tricks] a user into signing a transaction that delegates approval of the user’s tokens to the attacker.”
The recent $120m attack on BadgerDAO, for example, relied on a malicious injected script to enable ice phishing, which involved prompting users of the BadgerDAO web app to delegate the attacker to conduct transactions for them.
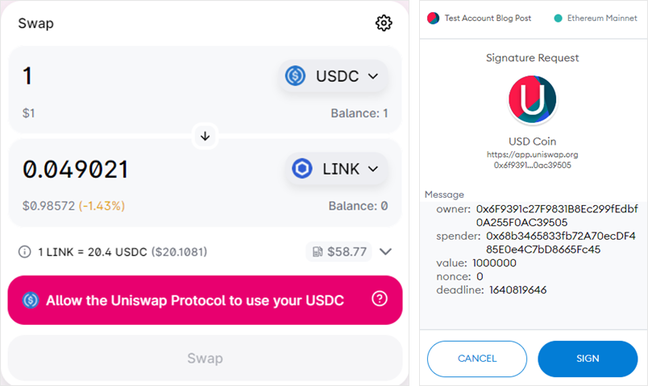
“In an ‘ice phishing’ attack, the attacker merely needs to modify the spender address to the attacker’s address,” said Christian Seifert, a security researcher at Microsoft, in a blog post. “This can be quite effective as the user interface doesn’t show all pertinent information that can indicate that the transaction has been tampered with.”
Seifert said Badger’s smart contract front-end infrastructure at Cloudflare was compromised and the attacker gained control over a Cloudflare API key. That allowed the injection of a malicious script into the Badger smart contract front end.
“This script requested users to sign transactions granting ERC-20 approvals to the attacker’s account,” explained Seifert.
ERC-20 refers to the standard for creating smart contracts on the Ethereum blockchain. ERC-20 tokens implement an API for smart contracts which allow programmatic transactions. The token owner can transfer tokens but must delegate authority to any smart contract that would transact on the owner’s behalf.
In the BadgerDAO theft, almost 200 individuals ended up handing control of their tokens to a smart thief instead of a smart contract. They did so because the app interface didn’t make it obvious that the “spender” account being authorized was controlled by the attacker.
Seifert also described other forms of cybercrime tuned for “web3,” which is to say decentralized finance and related blockchain jargon.
There’s scanning social media for people seeking support with wallet software and responding with spoofed support messages in the hope of convincing the victim to reveal private crypto wallet keys. There’s distributing new tokens for free and then causing transactions involving those tokens to fail with an error message that redirects to a phishing site or malware installer. And there’s impersonating legitimate smart contract front ends or wallet software to nab private keys directly.
Really, it’s all just the same old web, code, and scammers. But feel free to call it web3 if that makes it seem shiny and new.
Microsoft at least has an idea about how to mitigate cryptocurrency-focused attacks. The company has created and open-sourced an agent on Forta, a smart contract threat-detection platform. The software looks for suspicious token approvals – the precursor of ice phishing – and suspicious transfers. Maybe this will help.
Seifert also offers web3 users advice on protecting themselves from threats like the BadgerDAO attack. Mostly it’s common sense stuff like “Review the smart contract you are interacting with.” This seems likely to be about as successful as “Review the code in your npm dependencies.”
But Seifert also calls out a real problem with the entire web3 ecosystem, the lack of consumer protection.
“[T]hese recommendations put a lot of burden on the users; we encourage web3 projects and wallet providers to increase usability to help users perform these actions,” he said.
In the meantime, we recommend either Rekt or “web3 is going just great” for those interested in keeping up with the crypto thefts and scams fueling the web3 dumpster fire. ®
Microsoft offers defense against ‘ice phishing’ crypto scammers
Source: Expert Gwapo Pinoys
0 Comments